Strangler Fig Pattern Explained: Modernize Legacy Systems Safely
Introduction: The Legacy System Problem Nobody Escapes
Almost every successful company has one thing in common:
👉 A legacy system they’re afraid to touch.
It might be:
A 10-year-old monolith
A critical billing system
A tightly coupled ERP
A “don’t touch or it breaks” application
Rewriting everything at once sounds tempting — but in reality, it’s risky, expensive, and dangerous.
That’s exactly why the Strangler Fig Pattern exists.
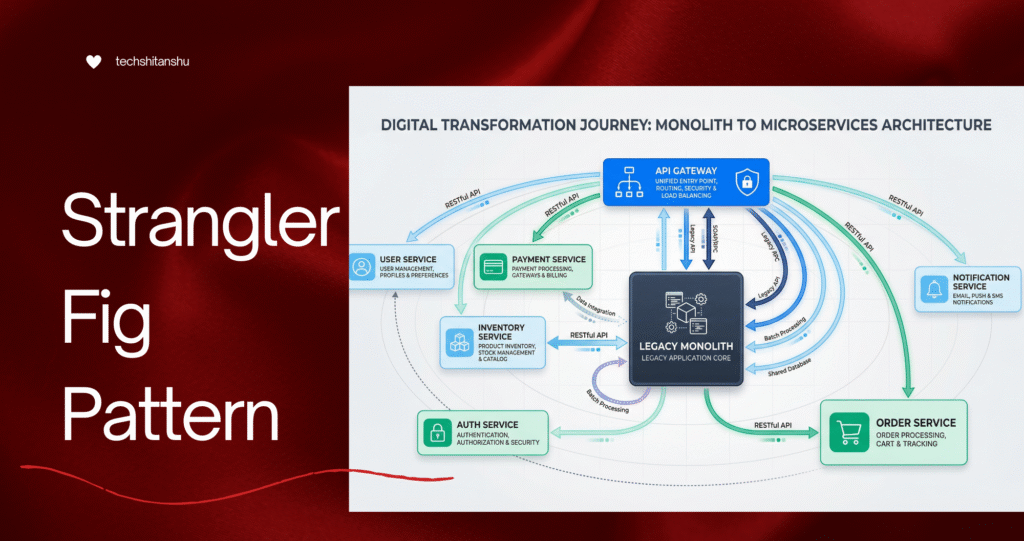
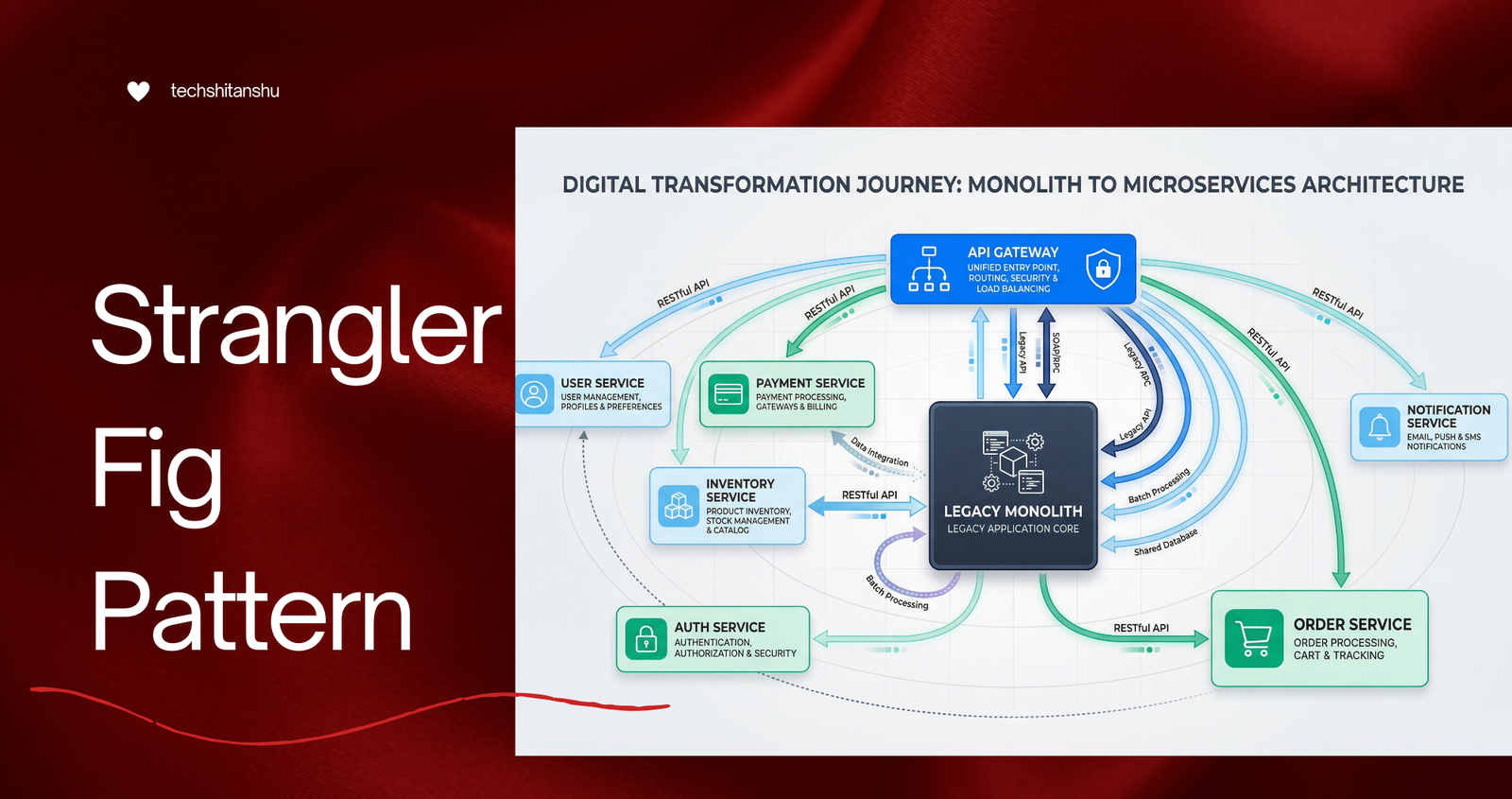
What Is the Strangler Fig Pattern?
The Strangler Fig Pattern is an architectural strategy for incrementally modernizing legacy systems.
Instead of rewriting the entire system:
You gradually replace parts
New functionality “strangles” the old system
The legacy app slowly fades away
Why the Name?
It’s inspired by the strangler fig tree, which grows around an old tree and eventually replaces it — without killing it immediately.
Why Enterprises Love This Pattern
This pattern directly supports:
Cloud migration projects
Microservices adoption
Digital transformation
Risk-controlled modernization
That’s why it attracts high-value enterprise ads related to:
Cloud platforms
SaaS tools
Security
DevOps & observability
The Core Idea (Simple Explanation)
Instead of:
❌ Big-bang rewrite
You do:
✅ Small, controlled replacements
Step-by-Step:
Route traffic through a facade (API Gateway / proxy)
Build new services for specific features
Gradually redirect traffic
Retire legacy components safely
Strangler Fig Architecture (High-Level)
Client
|
API Gateway / Router
|
-----------------------
| |
New Microservices Legacy Monolith
Over time:
More traffic → new services
Less traffic → legacy system
Eventually → legacy system is gone
Real-World Example: E-Commerce Modernization
Before
One giant monolithic app
Slow releases
High risk deployments
Migration Using Strangler Fig
| Phase | Action |
|---|---|
| 1 | Extract product catalog |
| 2 | Extract authentication |
| 3 | Extract order management |
| 4 | Keep billing last |
Each release delivers business value — without downtime.
Why the Strangler Fig Pattern Works So Well
1️⃣ Low Risk Migration
You replace small pieces, not everything.
2️⃣ Continuous Delivery
No long freeze periods.
3️⃣ Business Continuity
Customers never notice the change.
4️⃣ Flexible Technology Choice
Each new service can use modern stacks.
5️⃣ Cost Control
Modernize gradually — not all at once.
Strangler Fig vs Big-Bang Rewrite
Aspect | Big-Bang Rewrite | Strangler Fig |
|---|---|---|
Risk | Extremely High | Low |
Time to Value | Long | Continuous |
Downtime | Likely | Minimal |
Cost Predictability | Poor | High |
Enterprise Adoption | Rare | Very Common |
Where the Pattern Fits Best
✔️ Legacy monoliths
✔️ Mission-critical systems
✔️ Enterprises with uptime requirements
✔️ Regulated industries (finance, healthcare)
Key Components of a Successful Strangler Pattern
🔹 Routing Layer
API Gateway
Reverse proxy
Load balancer
🔹 Feature-Based Decomposition
Migrate features, not technical layers.
🔹 Strong Monitoring
Track traffic shifts and errors.
🔹 Contract Testing
Ensure new services behave exactly as expected.
Common Migration Strategies
Route by URL
Example:/api/v2/* → new services
Route by Feature
Example:
Payments → new service
Reports → legacy
Route by User Segment
Beta users → new system
Others → legacy
Challenges You Must Plan For
Increased Operational Complexity
You’ll run two systems in parallel for a while.
Data Synchronization
Shared data must be handled carefully.
Team Coordination
Clear ownership is critical.
Best Practices (Enterprise Grade)
✔️ Start with low-risk features
✔️ Keep legacy stable
✔️ Use feature toggles
✔️ Maintain backward compatibility
✔️ Invest in observability
✔️ Document migration stages
Strangler Fig + Modern Cloud Stack
This pattern works beautifully with:
Kubernetes
API Gateway Pattern
BFF Pattern
Database per Service
CQRS
Event-Driven Architecture
It’s often the first step toward microservices.
FAQs
❓ Is Strangler Fig Pattern only for microservices?
No. It works for any modernization, including modular monoliths.
❓ How long does strangling take?
Anywhere from months to years — depending on system size.
❓ Can legacy and new systems share a database?
Avoid it. Use APIs or events instead.
❓ Is this pattern expensive?
It’s cheaper than failed rewrites.
❓ When should I stop strangling?
When no traffic reaches the legacy system.
Final Thoughts
The Strangler Fig Pattern is not about speed — it’s about survival and success.
If your system is:
Too critical to rewrite
Too slow to evolve
Too risky to replace overnight
This pattern gives you a safe, proven escape path.
“Part of our Microservices Design Patterns Series.”

Leave a Reply